Abstract, Disclaimer, Warning
The following document describes an advanced technique to setup a Google account to rely on solely the information from a password manager i.e. no phone and no “real” second factor. This is only reasonable for cases where there is either no other alternative i.e. no other trustworthy device that could be used for the login or no sense in protecting the account as nothing of interest is stored/associated with it.
I believe it to be patronizing of Google to assume that the account you create there is so important that it requires world-class security mechanisms that not even banks require. Yet it cannot be denied that for many people the data of the account will be in fact at least as important as their bank account.
You have been warned.
The Problem
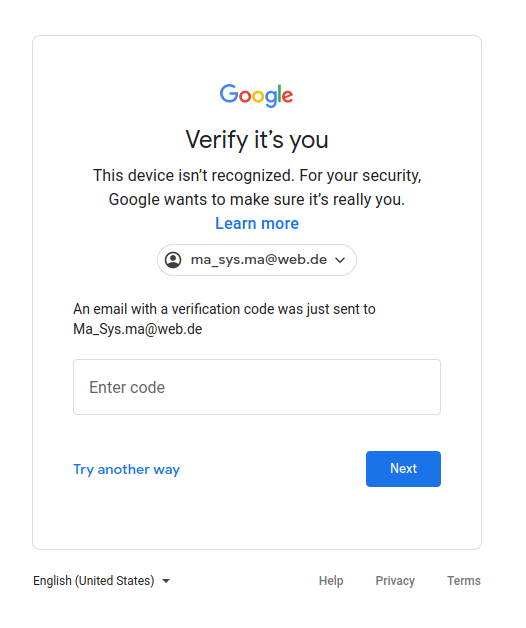
I was repeatedly presented with the following screens when trying to login with my Google account:
- Username
- Password
- Submit verify code to e-mail
From: Google <noreply@google.com>
To: Ma_Sys.ma@web.de
Subject: Google-Bestätigungscode
Lieber Google-Nutzer,
wir haben eine Anfrage für den Zugriff auf Ihr Google-Konto
ma_sys.ma@web.de über Ihre E-Mail-Adresse erhalten. Ihr
Google-Bestätigungscode lautet:
YYYYYYWith YYYYYY being the code to enter.
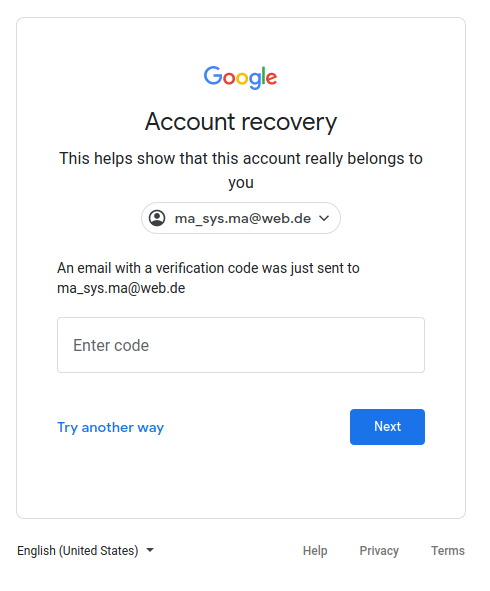
- Enter verify code
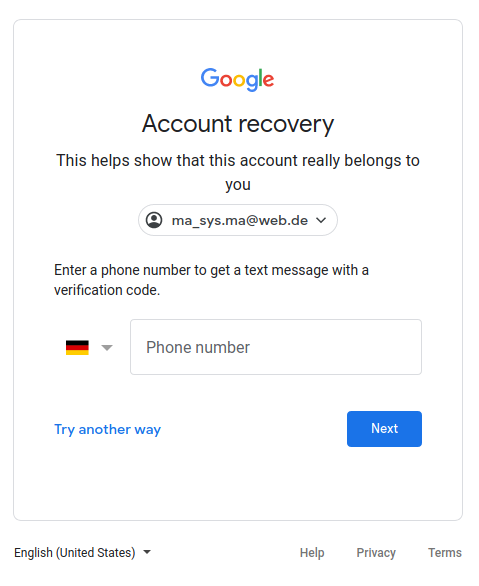
- Not enough information OR ALTERNATIVELY enter a phone number
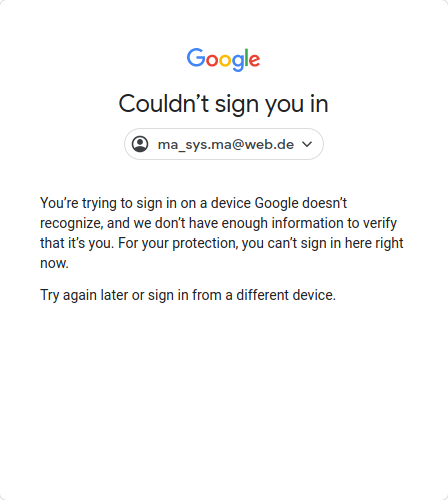
Some freely available phone numbers for receiving SMS online did not work (“That number has been used too often”). After giving up at the phone number screen, I always received an e-mail as follows:
From: Google <no-reply@accounts.google.com>
To: Ma_Sys.ma@web.de
Subject: Critical security alert
Sign-in attempt was blocked
Someone just used your password to try to sign in to your account.
Google blocked them, but you should check what happened.Followed by a link that lead to said login screen again. Thank you, Google! That someone was me… Login to that account seems to be lost permanently.
Interestingly, it was also not possible to create a new account with a secure Firefox configuration that rejects most tracking and loses its cookies upon exit. But: Starting with a new Firefox profile it suddenly became possible to create an account.
Creating an Account Without Phone Number
- Disable all blocking things by using a new Firefox profile.
(Sledgehammer approach:
mv ~/.mozilla ~/.mozilla.bak) - Try to create an account
- Observe telephone number field becomes optional
Keeping the Account: Enabling TOTP 2FA the hard Way
It can be foreseen that access to the account will be lost if no measures are taken to allow some further “verification” beyond the simple e-mail because e-mail alone is known not to be enough.
My initial idea was to use TOTP because TOTP seeds can be stored in a
password manager and that can be used together with
oathtool to login.
Upon trying to configure 2FA in Google however, I am presented with a screen that only allows these types of 2FA:
- Phone Number + SMS
- Phone Number + Phone Call
- Hardware Token
- App on Smartphone (Not a TOTP-based authenticator!)
The solution here is as hacky as it gets: Chose Hardware Token.
Notes about using Rust U2F
Emulate a hardware token using an application e. g. https://github.com/danstiner/rust-u2f.
- Download deb files (alternatively might want to generate them yourself, recommended)
- Install all deb files (alternatively follow the
curl | bashway, NOT recommended) - Enable and start the services with systemd:
systemctl daemon-reload
systemctl enable softu2f.socket
systemctl --user daemon-reload
systemctl --user start softu2f- Run on KDE. Or another heavy Desktop Environment: i3, icewm, LXDE is all not enough! Rationale: Otherwise the approve-option will be missing from the notification dialogs (you will notice it appearing as a red rectangle box with no interaction possible)
- I could not find out where the secret data of the emulated hardware token are stored.
- It can happen that the user service
softu2fcrashes, in that case restart it and try again:systemctl --user restart softu2f
Continue setting up the Token for Google
Follow the instructions for setting up the Hardware Token in Google.
After completion, additional options for 2FA for Google become available.
- Now add an authenticator app (I chose Android)
- Press I cannot scan the code
- Retrieve the TOTP seed (ignore/remove the spaces!)
- Use
oathtool --base32 --totp <seed>to retrieve six digit code. - Complete Google’s setup process by testing with a freshly generated six digit code.
Now as the last step, it is possible to remove the hardware token from Google to obtain the desired state: Login via username+password+TOTP.
Epilogue
For me personally, the experience with Google Login has drained my trust in Google accounts to zero. An login that I cannot perform with providing the correct password and e-mail verification is simply unacceptable. Giving more personal data to Google is not acceptable, either.
Yet there are occasions today where the use of Google seems to be inevitable (ever tried to install an Android “App” without? – possible, but difficult!) hence the necessity to retain an account and stay tuned to whatever new loopholes are required to login.